System Settings
Authority Management
The authority management module is used to manage users who are allowed to log in to the Multi-tenant Management Backend and their respective permissions within the platform.
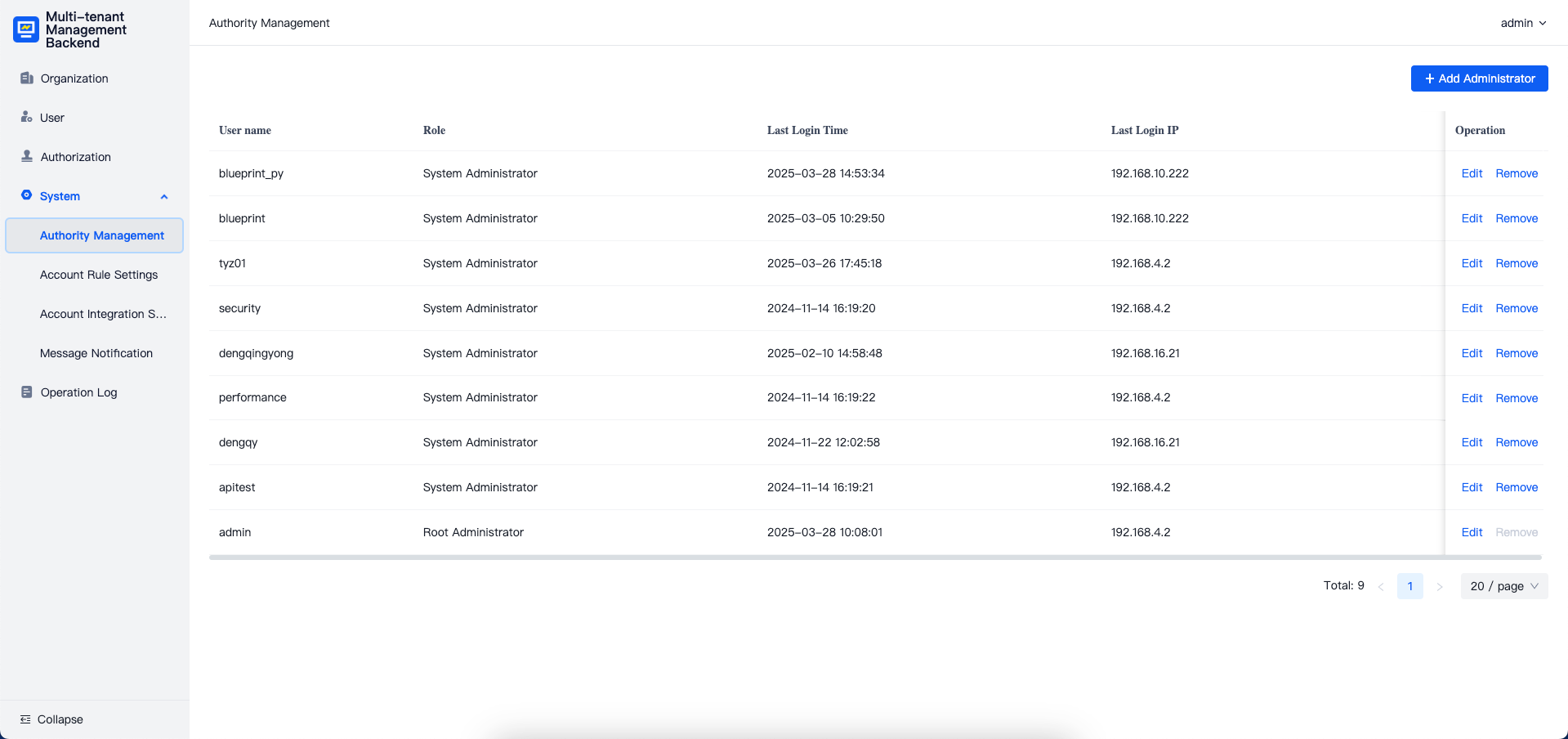
Add Administrator
Click the "Add Administrator" button in the upper right corner to add a new administrator.
In the pop-up "Add Administrator" dialog, select the administrator role and click the "Generate Link and Copy" button to create an invitation link for adding an administrator. If the user has already registered an account, they can directly join the organizational system as an administrator by clicking the invitation link. If the user has not yet registered, they will need to complete the registration process using a username, email, etc. Note that the invitation link is valid for 3 days; a new link must be generated if it expires.
The available roles are:
- System Administrator: Has full permissions within the Multi-tenant Management Backend.
- Organization Administrator: Only has permissions for the "Organization Management" and "User Management" pages within the Multi-tenant Management Backend.
Edit Administrator
Click the "Edit" button under any user to modify the user's assigned role.
Remove Administrator
Click the "Remove" button under any user to remove them from the Multi-tenant Management Backend. After removal, the user will lose the ability to log in to the Multi-tenant Management Backend.
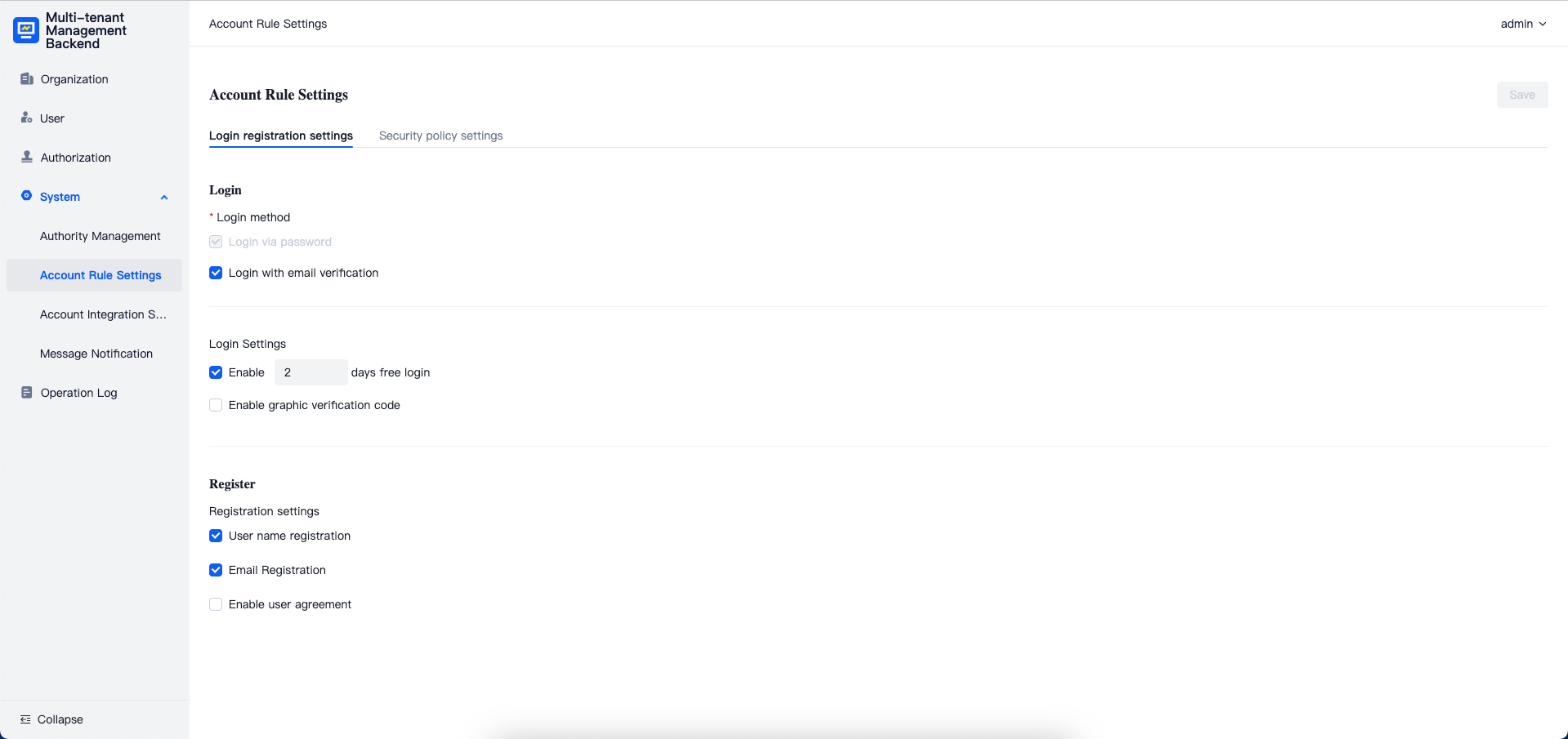
Account Rules Settings
The account rules settings module is used to manage configurations related to user account login, registration, and security policies. Details are as follows:
Login and Registration Settings
Supported registration methods include:
- Username registration
- Email registration
- Registration without invitation
Select the corresponding options in the login and registration module to enable the related registration methods. For email registration, you can choose whether to enable email verification. If enabled, you can also configure whether login requires email verification.
In addition to registration and login methods, the system supports the following configurations:
- Password recovery functionality
- Login session duration settings
- User agreement activation
- CAPTCHA settings
Account Rule Settings
Security policies can be customized and include the following options:
- Minimum account length
- Password expiration period
- Password complexity requirements
- Maximum consecutive password errors
- Account lockout duration due to password errors
Account Integration Settings
The account integration settings module supports SSO (Single Sign-On) integration between platform users and external accounts. Integration can be achieved using the following protocols:
- LDAP
- OAuth2 (including OIDC)
The status of the current integration method (enabled or disabled) can be viewed on the integration method card. Only one integration method can be enabled at any given time.
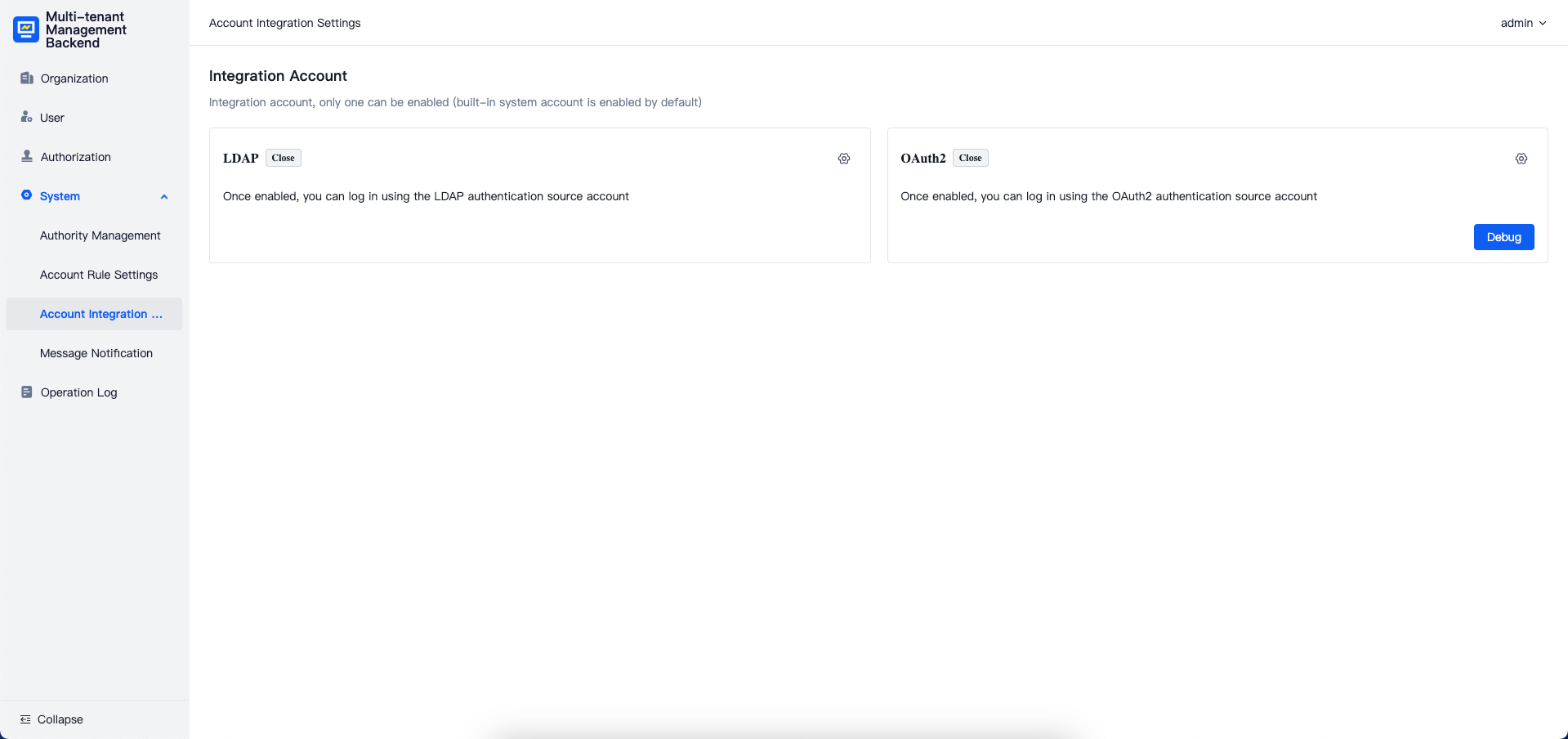
To enable third-party account integration, click the settings icon in the upper-right corner of the desired integration method card, navigate to the settings page, select "Enable", and click "Save."
LDAP Integration
Supports integration of external LDAP accounts with platform users. Features include:
- Testing the connection to the LDAP service
- Configuring LDAP user group filters
- Setting up organizational and role configurations within the platform upon successful LDAP integration
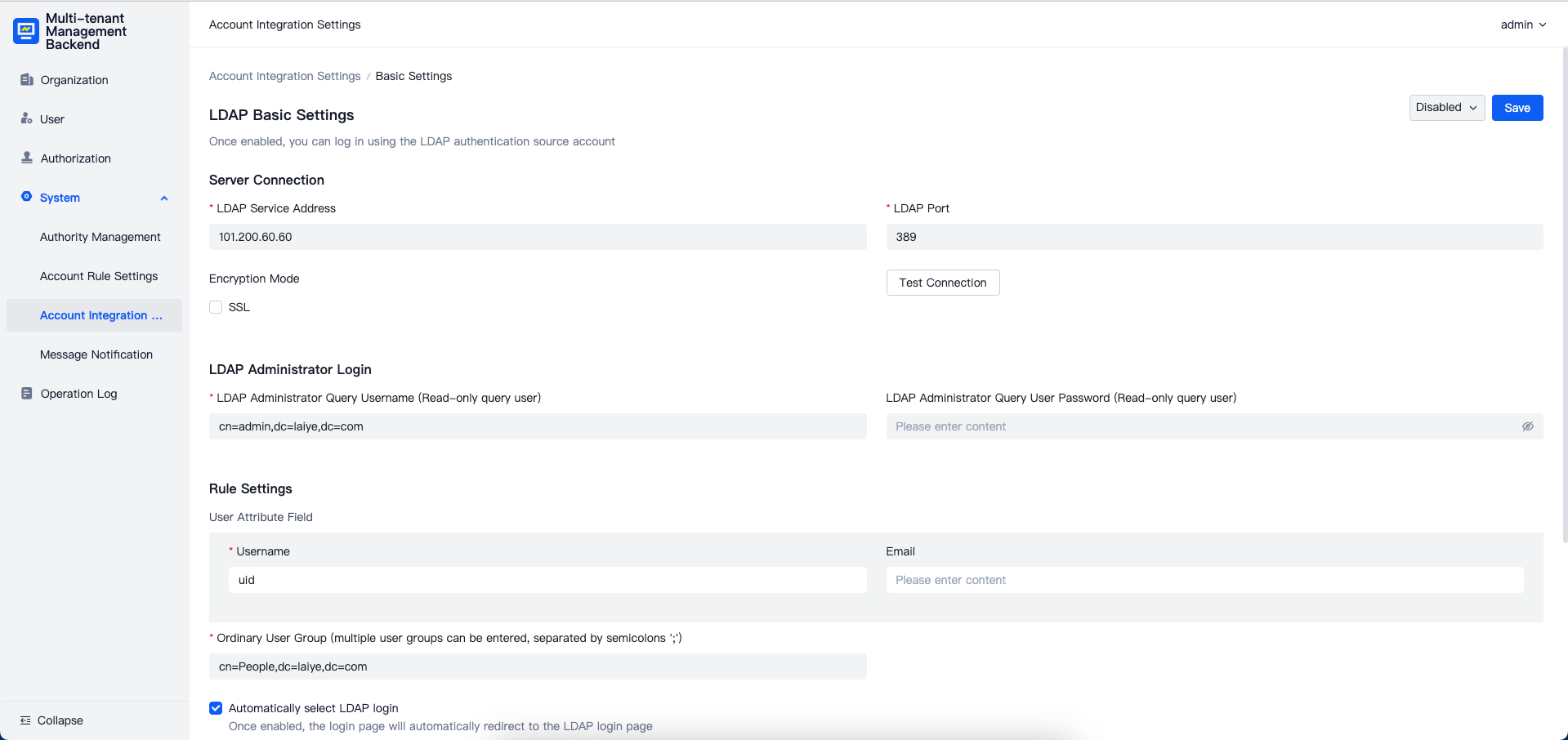
LDAP Management Settings
Supports mapping configurations between LDAP user information and platform user fields. For example, platform username and email fields can be mapped to LDAP user field IDs. Additionally, LDAP user group whitelists can be configured. LDAP users not in the whitelist will be unable to log in successfully.
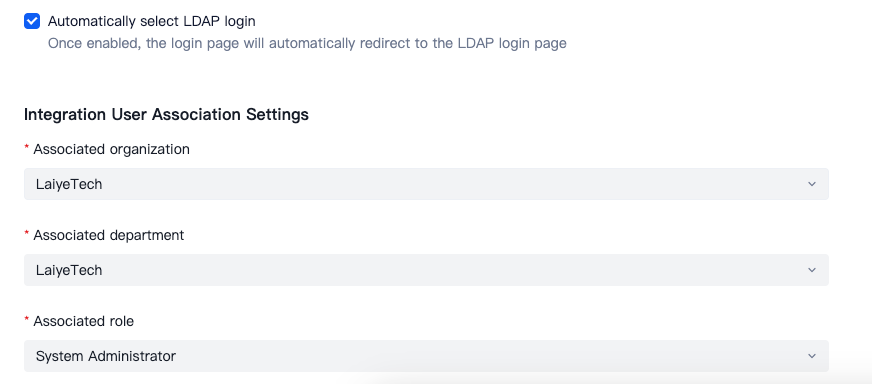
User Association Settings
Configure default organizational and departmental assignments, as well as roles, for LDAP accounts upon their first login.
LDAP Login Instructions
After completing LDAP integration, users can select "LDAP Login" under the "Other Login Methods" option in the following interfaces:
- Intelligent Automation Platform
- Floating License-Automation Worker
- Floating License-Automation Creator
After users log in, administrators can view member information in the user management module. Members will be associated with the corresponding organization and department based on the "User Association Settings." If modifications to member permissions or organizational associations are needed, edits can be made.
Note: Members will only appear in the system once they complete a full LDAP login process.

LDAP integration uses an external account binding approach with internal system users. During the first login, the system will prioritize binding with an internal user of the same name; if no such user exists, a new internal user will be automatically created and bound. For example, if the external account username is "zhansan3," the system will attempt to bind with an internal user named "zhansan3." If no such user exists, a new internal user "zhansan3" will be created and bound.
To delete an external account, go to "Multi-tenant Management Backend" > "User Management," unbind the internal user from the third-party account, and then delete the internal account.
Internal system users adhere to account rules and support password modification and reset operations. Since the password for internal users is randomly generated upon creation, administrators can assist with password resets. Internal accounts can also access the system using their original login methods.
OAuth2 Integration
Supports integration with external accounts using the OAuth2 protocol and can integrate with platforms such as DingTalk, WeCom, and Lark that support OAuth2.
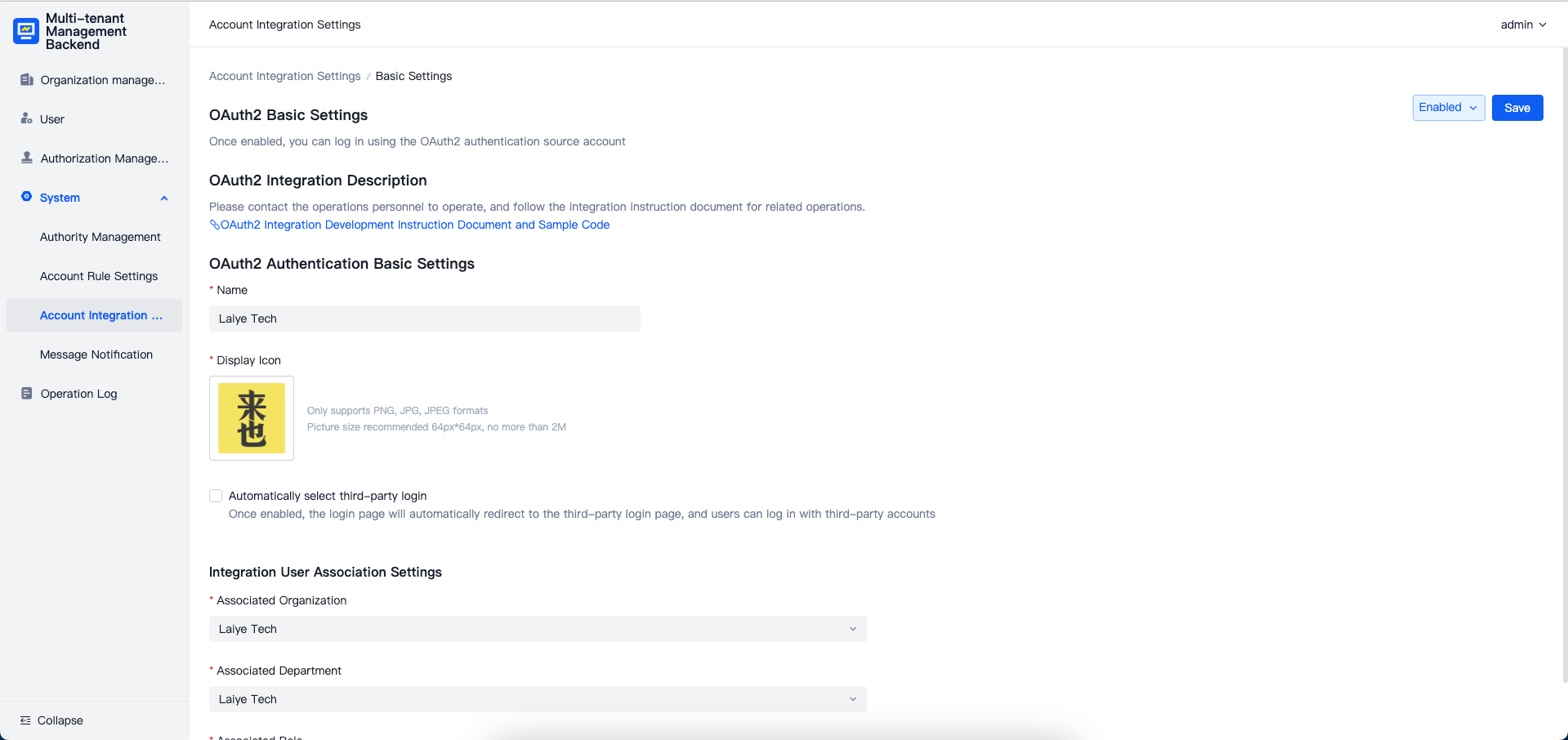
Click the "OAuth2 Integration Development Documentation" link to download the relevant package, which includes example Python code and instructions for integrating with WeCom, DingTalk, and Lark.
Debugging
By default, the debugging feature is disabled. Contact the operations engineer to enable this feature. Once enabled, OAuth2 integration debugging can be performed.
The debugging module supports uploading Python scripts for integration with external accounts that support the OAuth2 protocol and provides debug logs to help developers optimize their code.
Upload Debug Script
Supports uploading Python script files. After uploading, the specific Python code content can be viewed in the interface.
Debug Logs
Supports querying logs using log levels, time ranges, and log content.
OAuth2 Login Instructions
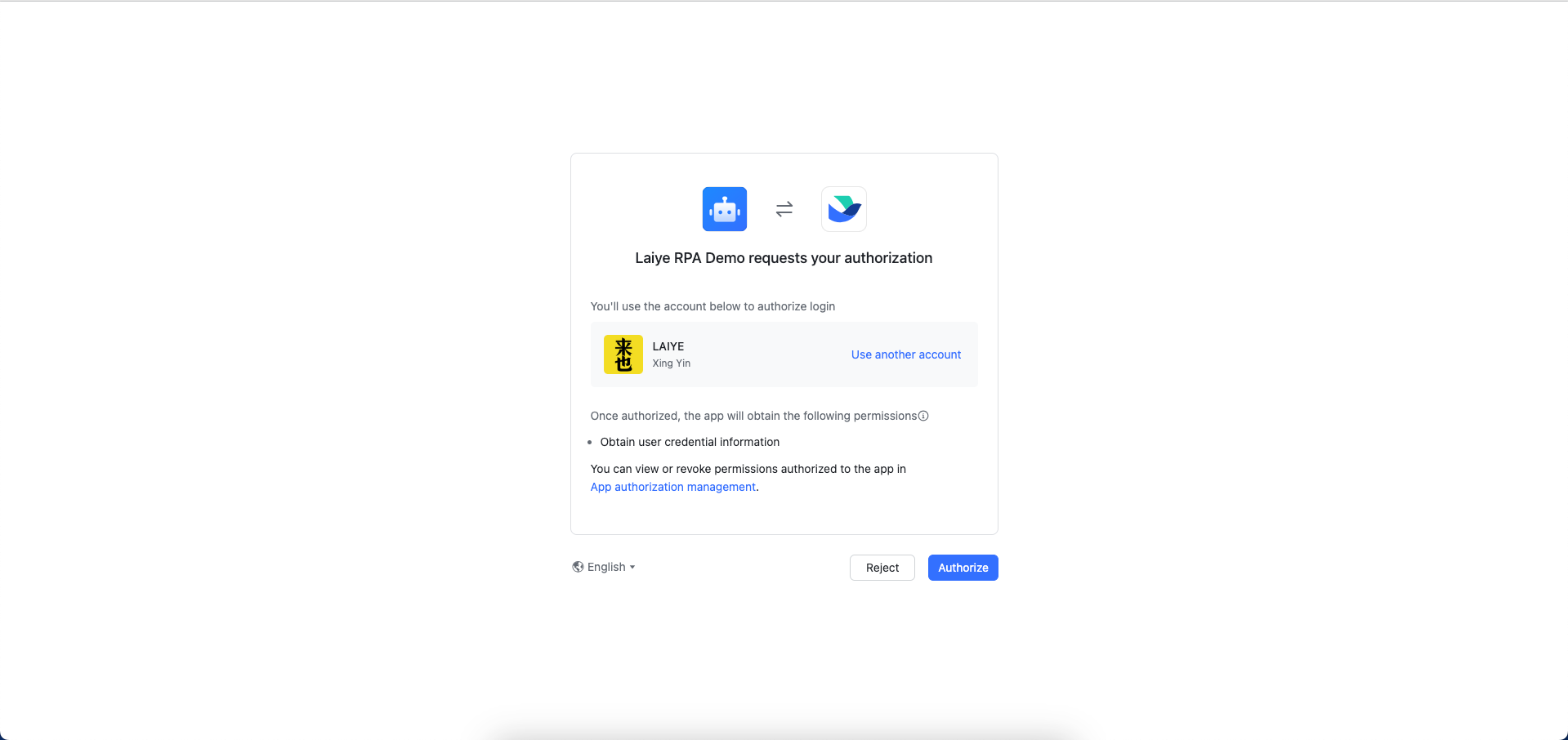
After completing OAuth2 integration, users can log in using the OAuth2 login method via the "Other Login Methods" option. The example below demonstrates logging in via Lark:
The Lark will guide you to finis authorithing in a new tab page: